Data Management
Generally Cortex Data Management is composed of:
- Data Pipeline Configuration and Management: Manage Data Pipeline
- Data Policy Creation and Management: Manage Data Policy
These are most powerful when used together, with Configuration mapping context from Data Pipelines and/or Data Transformation to Data Policies.
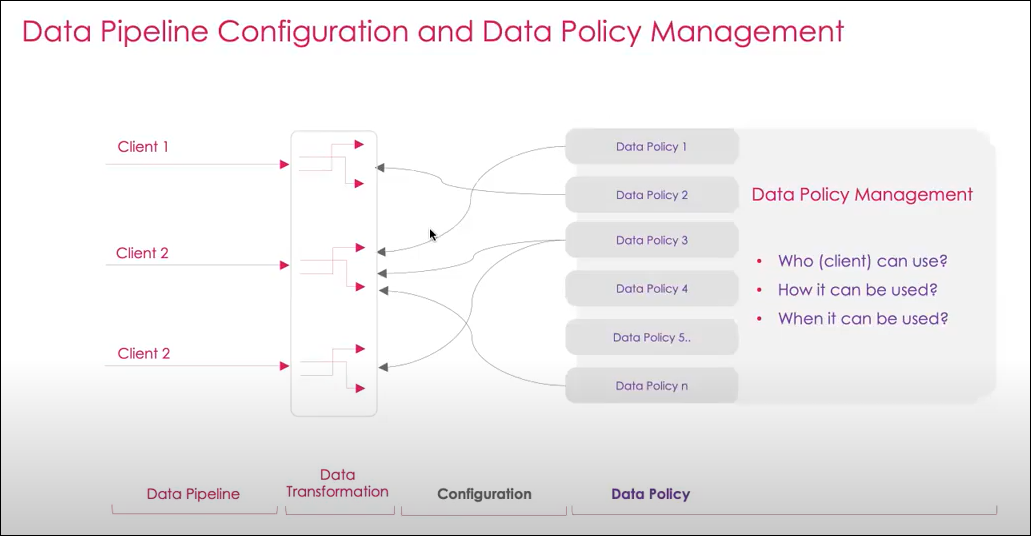
Key Concepts from the above graphic:
- Data Policies and Data Pipelines are configured and exist independently of each other
- Data Policy only applies when it is associated with Data Pipelines with Transformation Configuration
- All Transformation Configurations have to have a Data Policy
- Data Policies are Customer-specific and cannot be applied to Transformation Configuration that does not belong to the Customer
Data Pipelines
Data flows to Adara through Data Pipelines. Data Pipeline Management determines the endpoints between which the data pipeline flows from clients to Adara. Most clients have multiple data pipelines with different streams of discrete data. Clients can upload specific files to Adara as well, but high-volume data flows best through Data Pipelines. See Manage Pipeline for an example of a data pipeline.
Data Policy Management
Data Policy Management determines how customer data can be used once it arrives at Adara:
- who can use the data
- how they can use the data
- when can they use the data
Clients with multiple pipelines can use different data policies for different data pipelines. Data policies can manage permissions across any combination of permission level, including Use Case, Consortium, Vertical, Customer, Account, and/or Platform. See Manage Policy for an example of a data policy.
Data Transformation
Data transformation can be configured to occur on Adara servers as part of a Data Policy. All Transformation Configurations have Data Policy but not all Data Policies include Transformation Configurations. See Manage Transform Configuration for an example of a transform configuration.
Data Configuration
Data Configurations....
Data Rights Management
Managing data pipelines, data policies, and data transformations separately allows precise management of these elements individually or in group and across any combination of permission level (Use Case, Consortium, Vertical, Customer, Account, and/or Platform). Adara built Cortex Data Management to deliver full accountability and provenance for data, as well as full control of how that data is shared and/or used.
Data Provenance
Adara Data Polices and Derived Policies exist and persist in context to data pipelines and not just at the point of data utilization. Cortex Data Management explicitly and persistently tracks policy origins, chain of custody, and context for the entire life of the data while it exists on Adara servers, allowing true data provenance: a chronology of the ownership, origins, custody, context, transformations, and delivery of data.